Yubikey for Django
on 11 december 2019 10:44
Security is one of the biggest problems of todays computer and internet usage. Bad passwords, reuse of passwords across sites and keylogging to steal passwords are some of the reasons that people are hacked.
“We have had no reported or confirmed account takeovers since implementing security keys at Google”,
a spokesperson told TechCrunch.
After reading this I decided to start using a hardware security key. The Google Titan hardware key is not available in the Netherlands, and the SOLO key was not yet finished. But the YubiKey exists already for a while and can easily be ordered. I ordered two , so I would have a backup.
I ordered the Yubikey 5 NFC that supports the FIDO2 U2F login, but also OTP (One Time Password) functionality. And it can use NFC, so you can also use it for your Android devices that do not have a USB port.
For now I enabled it for my Google and Github accounts. There is was easy to add Yubikey as second factor.

For my general password store I use Keepass and I switched to KeepassXC where is is possible to secure the password database with a Yubikey. So even when my Keepass database is stolen en the password for this database was obtained by keylogging, hackers still have no access to my passwords in there.
You have to configure one of your YubiKey slots for HMAC-SHA1 Challenge Response mode and I configured both my Yubikeys in the same way, so I still have access to my KeepassXC when one of the keys is lost. You can also make a backup of your code and store it in your safe.
For Facebook, LinkedIn, Slack, XS4All and many others I could not yet find a way to use my Yubikey as 2nd factor. There is still work to do!!
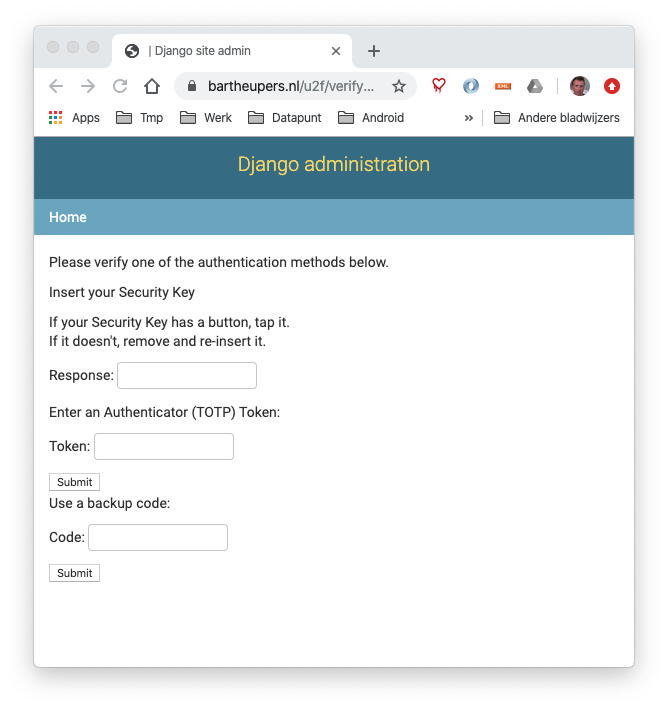
As part of this work I secured this website with Yubikey 2nd factor authentication. This website is a Django powered website, where you can login to access admin functionality. For example to write this blog.
A Django app can be secured for U2F login with the Django U2F module. Just follow instructions and after logging in normally add your security key(s), and create some backup codes.
In my production setup I also had to run the django-admin collectstatic again, because for the U2F login also a lot of custom javascript is required. But after that it works nicely.
It would also be nice to have a VPN login secured by a Yubikey. Until now I have not been successful in enabling this with my OpenVPN and Tunnelblick packages, although it should be possible. Perhaps in a future blog I will report again.